首先创建traefik来代理网络:
1
2
3
4
5
6
7
8
9
|
tree
.
├── config
│ ├── dashboard.lab.com.toml
│ ├── default.toml
│ └── tls.toml
├── docker-compose.yaml
├── ssl
└── traefik.toml
|
docker-compose.yaml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
version: '3.7'
services:
traefik:
container_name: traefik
image: traefik:v2.1.3
restart: always
ports:
- 80:80
- 443:443
networks:
- traefik
command: traefik --configFile /etc/traefik.toml
volumes:
- /var/run/docker.sock:/var/run/docker.sock:ro
- ./ssl/:/data/ssl/:ro
- ./traefik.toml:/etc/traefik.toml:ro
- ./config/:/etc/traefik/config/:ro
healthcheck:
test: ["CMD-SHELL", "wget -q --spider --proxy off localhost:8080/ping || exit 1"]
# 先创建外部网卡
# docker network create traefik
networks:
traefik:
external: true
|
当然,作为服务网关,得有服务健康自检,默认的时间太长,建议每 3~5 秒检查一次。
而 Traefik 2.0 支持从目录读取配置、支持动态加载,所以类似上面的问题就不存在了,只要对配置做好静态、动态配置拆分就好了,先来看静态配置 traefik.toml :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
[global]
checkNewVersion = false
sendAnonymousUsage = false
[log]
level = "WARN"
format = "common"
[api]
dashboard = true
insecure = true
[ping]
[accessLog]
[providers]
[providers.docker]
watch = true
exposedByDefault = false
endpoint = "unix:///var/run/docker.sock"
swarmMode = false
useBindPortIP = false
network = "traefik"
[providers.file]
watch = true
directory = "/etc/traefik/config"
debugLogGeneratedTemplate = true
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.https]
address = ":443"
|
tls.toml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
[tls]
[tls.options]
[tls.options.default]
minVersion = "VersionTLS12"
maxVersion = "VersionTLS12"
[tls.options.test-tls13]
minVersion = "VersionTLS13"
cipherSuites = [
"TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
"TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384",
"TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305",
"TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305",
"TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256",
"TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
]
[[tls.certificates]]
certFile = "/data/ssl/lab.io.crt"
keyFile = "/data/ssl/lab.io.key"
[[tls.certificates]]
certFile = "/data/ssl/lab.com.crt"
keyFile = "/data/ssl/lab.com.key"
|
default.toml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
[http.middlewares.https-redirect.redirectScheme]
scheme = "https"
[http.middlewares.content-compress.compress]
# tricks
# https://github.com/containous/traefik/issues/4863#issuecomment-491093096
[http.services]
[http.services.noop.LoadBalancer]
[[http.services.noop.LoadBalancer.servers]]
url = "" # or url = "localhost"
[http.routers]
[http.routers.https-redirect]
entryPoints = ["http"]
rule = "HostRegexp(`{any:.*}`)"
middlewares = ["https-redirect"]
service = "noop"
|
这个default.toml 把http转为https。
dashboard.lab.com.toml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
[http.middlewares.dash-compress.compress]
[http.middlewares.dash-auth.basicAuth]
users = [
"test:$apr1$H6uskkkW$IgXLP6ewTrSuBkTrqE8wj/",
"test2:$apr1$d9hr9HBB$4HxwgUir3HP4EsggP/QNo0",
]
[http.routers.dashboard-redirect-https]
rule = "Host(`dashboard.lab.io`, `dashboard.lab.com`)"
entryPoints = ["http"]
service = "noop"
middlewares = ["https-redirect"]
priority = 100
[http.routers.dashboard]
rule = "Host(`dashboard.lab.io`, `dashboard.lab.com`)"
entrypoints = ["https"]
service = "dashboard@internal"
middlewares = ["dash-auth", "dash-compress"]
[http.routers.dashboard.tls]
[http.routers.api]
rule = "Host(`dashboard.lab.io`, `dashboard.lab.com`) && PathPrefix(`/api`)"
entrypoints = ["https"]
service = "api@internal"
middlewares = ["dash-auth", "dash-compress"]
[http.routers.api.tls]
[http.routers.ping]
rule = "Host(`dashboard.lab.io`, `dashboard.lab.com`) && PathPrefix(`/ping`)"
entrypoints = ["https"]
service = "ping@internal"
middlewares = ["dash-auth", "dash-compress"]
[http.routers.ping.tls]
|
访问dashboard.lab.io
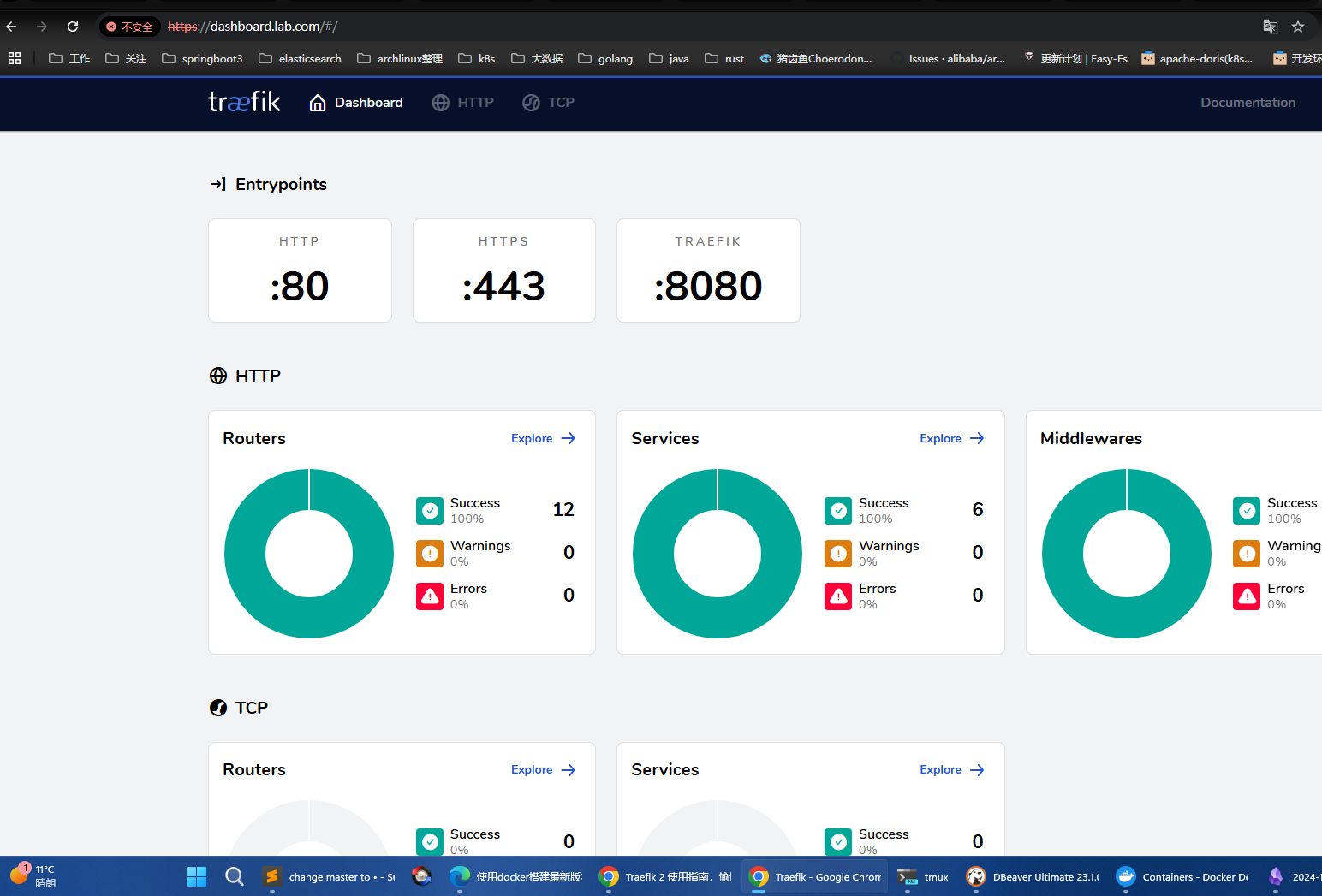 至此就基本完成了老配置 Traefik 的所有功能,后续如果有“规则”需要变化,只需要修改刚刚这几个文件即可,而无需重启 Traefik 就能生效了。
至此就基本完成了老配置 Traefik 的所有功能,后续如果有“规则”需要变化,只需要修改刚刚这几个文件即可,而无需重启 Traefik 就能生效了。
代码gitea的配置:
创建.env文件:
1
2
3
4
5
6
7
8
9
10
|
# 应用名称
SERVICE_NAME=Gitea
# 服务域名
SERVICE_DOMAIN=gitea.nuc.com
# 使用的应用镜像
DOCKER_IMAGE=gitea/gitea:1.13.2
# 允许公网,跨主机访问 Git SSH Server
#SSH_PORT_EXPOSE=22
# 仅允许内部 CI ,本地机器使用 SSH 访问服务
SSH_PORT_EXPOSE=127.0.0.1:22
|
接着来定义服务编排配置文件,一般情况下你只需要复制粘贴即可,而不需要调整:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
|
version: '3.6'
services:
gitea:
image: ${DOCKER_IMAGE}
container_name: ${SERVICE_DOMAIN}
ports:
- ${SSH_PORT_EXPOSE}:22
environment:
- USER_UID=1000
- USER_GID=1000
- APP_NAME=${SERVICE_NAME}
- RUN_MODE=prod
- RUN_USER=git
- SSH_DOMAIN=${SERVICE_DOMAIN}
- SSH_PORT=22
- SSH_LISTEN_PORT=22
- HTTP_PORT=80
- ROOT_URL=https://${SERVICE_DOMAIN}
- LFS_START_SERVER=true
- REQUIRE_SIGNIN_VIEW=true
- DB_TYPE=sqlite3
- INSTALL_LOCK=false
- DISABLE_GRAVATAR=true
networks:
- traefik
restart: unless-stopped
labels:
- "traefik.enable=true"
- "traefik.docker.network=traefik"
- "traefik.http.routers.giteaweb.middlewares=https-redirect@file"
- "traefik.http.routers.giteaweb.entrypoints=http"
- "traefik.http.routers.giteaweb.rule=Host(`${SERVICE_DOMAIN}`)"
- "traefik.http.routers.giteassl.middlewares=content-compress@file"
- "traefik.http.routers.giteassl.entrypoints=https"
- "traefik.http.routers.giteassl.tls=true"
- "traefik.http.routers.giteassl.rule=Host(`${SERVICE_DOMAIN}`)"
- "traefik.http.services.giteabackend.loadbalancer.server.scheme=http"
- "traefik.http.services.giteabackend.loadbalancer.server.port=80"
volumes:
# 标准 Linux 系统下使用
# - /etc/localtime:/etc/localtime:ro
# - /etc/timezone:/etc/timezone:ro
- ./repositories:/data/git/repositories
- ./data:/data/gitea/
logging:
driver: "json-file"
options:
max-size: "10m"
extra_hosts:
- "${SERVICE_DOMAIN}:127.0.0.1"
healthcheck:
test: ["CMD-SHELL", "wget -q --spider --proxy off localhost || exit 1"]
interval: 5s
networks:
traefik:
external: true
|
将上面的内容保存为 docker-compose.yml 后,使用 docker-compose up -d 来启动服务。
打开浏览器访问我们绑定的域名 “gitea.nuc.com” 可以看到服务已经启动就绪了。
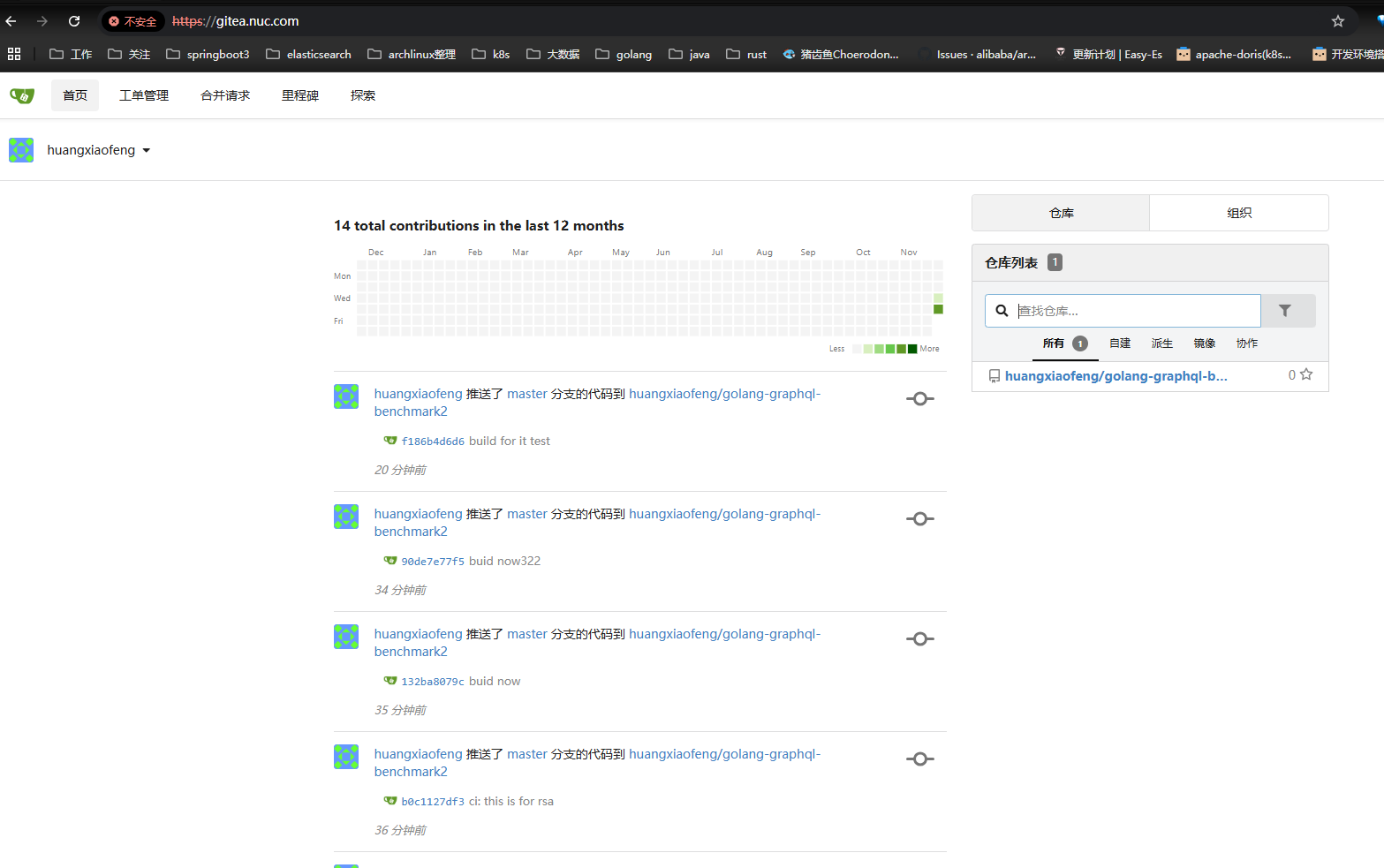
Drone 的服务端(Server)配置
同样的,先创建 .env 配置文件,这里有一部分内容,我们需要配置完 Gitea 后才能获取,所以你也可以选择在配置完 Gitea 后,再来完成下面的内容:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
# 服务域名
SERVICE_DOMAIN=drone.nuc.com
# 使用的应用镜像
DOCKER_IMAGE=drone/drone:1.10.1
# Drone 服务端和 Runner 之间通讯秘钥
DRONE_RPC_SECRET=YOUR_RANDOM_KEY
# Drone 超级管理员账号,根据自己需求修改
DRONE_ADMIN_USERNAME=soulteary
# Gitea 域名配置
GITEA_DOMAIN=gitea.nuc.com
# Gitea OAuth ClientID / Secret
# 稍后配置 Gitea 后替换即可
DRONE_GITEA_CLIENT_ID=a0da8a47-e89e-48ea-8ea3-08f2554511b1
DRONE_GITEA_CLIENT_SECRET=nrdSbAX_4AXexpUG_ZDw9iF640M8uC79h1raJxnX74I=
|
服务编排配置文件也比较简单,不需要做修改,直接复制粘贴到你的配置即可:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
|
version: '3.6'
services:
drone:
image: ${DOCKER_IMAGE}
container_name: ${SERVICE_DOMAIN}
environment:
- DRONE_GITEA_SERVER=http://${GITEA_DOMAIN}
- DRONE_GITEA_CLIENT_ID=${DRONE_GITEA_CLIENT_ID}
- DRONE_GITEA_CLIENT_SECRET=${DRONE_GITEA_CLIENT_SECRET}
- DRONE_LOGS_TRACE=true
- DRONE_AGENTS_ENABLED=true
- DRONE_RPC_SECRET=${DRONE_RPC_SECRET}
- DRONE_SERVER_HOST=${SERVICE_DOMAIN}
- DRONE_SERVER_PROTO=http
- DRONE_CLEANUP_INTERVAL=60m
- DRONE_CLEANUP_DISABLED=false
- DRONE_CLEANUP_DEADLINE_RUNNING=1h
- DRONE_CLEANUP_DEADLINE_PENDING=2h
- DRONE_USER_CREATE=username:${DRONE_ADMIN_USERNAME},admin:true
networks:
- traefik
restart: unless-stopped
labels:
- "traefik.enable=true"
- "traefik.docker.network=traefik"
- "traefik.http.routers.drone-web.middlewares=https-redirect@file"
- "traefik.http.routers.drone-web.entrypoints=http"
- "traefik.http.routers.drone-web.rule=Host(`${SERVICE_DOMAIN}`)"
- "traefik.http.routers.drone-ssl.middlewares=content-compress@file"
- "traefik.http.routers.drone-ssl.entrypoints=https"
- "traefik.http.routers.drone-ssl.tls=true"
- "traefik.http.routers.drone-ssl.rule=Host(`${SERVICE_DOMAIN}`)"
- "traefik.http.services.drone-backend.loadbalancer.server.scheme=http"
- "traefik.http.services.drone-backend.loadbalancer.server.port=80"
volumes:
# 标准 Linux 系统下使用
# - /etc/localtime:/etc/localtime:ro
# - /etc/timezone:/etc/timezone:ro
- ./data:/data
logging:
driver: "json-file"
options:
max-size: "10m"
extra_hosts:
- "${SERVICE_DOMAIN}:127.0.0.1"
healthcheck:
test: ["CMD-SHELL", "wget -q --spider --proxy off localhost:80/healthz || exit 1"]
interval: 5s
networks:
traefik:
external: true
|
因为我们尚未配置好 Gitea ,所以先不着急启动服务。
Drone 的客户端(Runner)配置
我们接着来配置 Drone Runner ,还是先创建一套 .env 文件:
1
2
3
4
5
6
7
8
9
10
|
# 服务域名
SERVICE_DOMAIN=runner.nuc.com
# 使用的应用镜像
DOCKER_IMAGE=drone/drone-runner-docker:1.6.3
# Drone 服务端和 Runner 之间通讯秘钥
DRONE_RPC_SECRET=YOUR_RANDOM_KEY
# Runner 最大并发数量,根据自己需求来
DRONE_RUNNER_CAPACITY=2
# Drone 服务配置域名
DRONE_SERVER_DOMAIN=drone.nuc.com
|
然后是定义容器编排配置文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
version: '3.6'
services:
drone-runner:
image: drone/drone-runner-docker:1.6.3
container_name: ${SERVICE_DOMAIN}
expose:
- 3000
environment:
- DRONE_RPC_PROTO=http
- DRONE_RPC_HOST=${DRONE_SERVER_DOMAIN}
- DRONE_RPC_SECRET=${DRONE_RPC_SECRET}
- DRONE_RUNNER_CAPACITY=${DRONE_RUNNER_CAPACITY}
- DRONE_RUNNER_NAME=${SERVICE_DOMAIN}
- DRONE_RUNNER_NETWORKS=traefik
networks:
- traefik
restart: always
volumes:
# 标准 Linux 系统下使用
# - /etc/localtime:/etc/localtime:ro
# - /etc/timezone:/etc/timezone:ro
- /var/run/docker.sock:/var/run/docker.sock
- ./data:/data
logging:
driver: "json-file"
options:
max-size: "10m"
extra_hosts:
- "${SERVICE_DOMAIN}:127.0.0.1"
healthcheck:
test: ["CMD-SHELL", "wget -q --spider --proxy off localhost:3000/healthz || exit 1"]
interval: 5s
networks:
traefik:
external: true
|
将上面的配置保存为 docker-compose.yml。和 Drone Server 一样,因为依赖 Gitea 配置,所以这里我们先不着急启动服务。
代码仓库 Gitea 的进一步配置
访问安装后的 Gitea,不论是点击“登陆”亦或者“注册”,界面都将会来到“初始配置”页面:https://gitea.nuc.com/install。
直到我们配置完毕后,应用才能够真正的开始提供服务。
初始化应用配置
那么来简单讲讲如何进行配置,以及配置过程中的一些细节。
数据库可以根据自己实际情况切换为更为可靠的 PostgreSQL,如果你是个人或者小团队使用,使用 SQLite 问题也不大。
“一般设置”默认已经根据前文中的内容,进行了的自动化填充,这里如果还是想修改,仅建议修改 “站点名称”, 其余内容不建议进行修改。
“可选设置”包含三类配置项目:
- “可选设置”中的“电子邮箱设置”可以根据你的实际情况完成配置,如果是个人使用,或者现在不想配置,可以先跳过,后续我们将配置更好用的推送通知,不依赖这个配置。
- “可选设置”中的“服务器和三方设置”,我个人建议勾选“启用本地模式”,其余内容根据自己喜好来勾选即可,如果是个人使用,可以将各种注册方式都去掉。
- “可选设置”中的“管理员账号设置”是必须完成配置填写的,填写方式可以参考下面的模式,建议全部使用小写英文,避免后续应用升级后出现预期之外的功能问题。
还记得前文中我们迟迟没有启动的 Drone Server 和 Drone Runner 吗?前文中我们在 Drone Server 中设置了一套 OAuth ClientID / Secret 变量,当我们正确设置了 OAuth 变量后,Drone 便能够根据 Gitea 进行自动的仓库、用户的创建和管理,而无需我们再进行手动配置。
某种程度来看,Drone 可以看作一套无状态的服务,这方便了后续我们扩容或者同类服务切换的可能性。
下面来就来讲讲如何配置跨应用授权。
点击右上角的个人用户头像,选择下拉菜单中的“设置”,在新页面中选择“应用”选项。
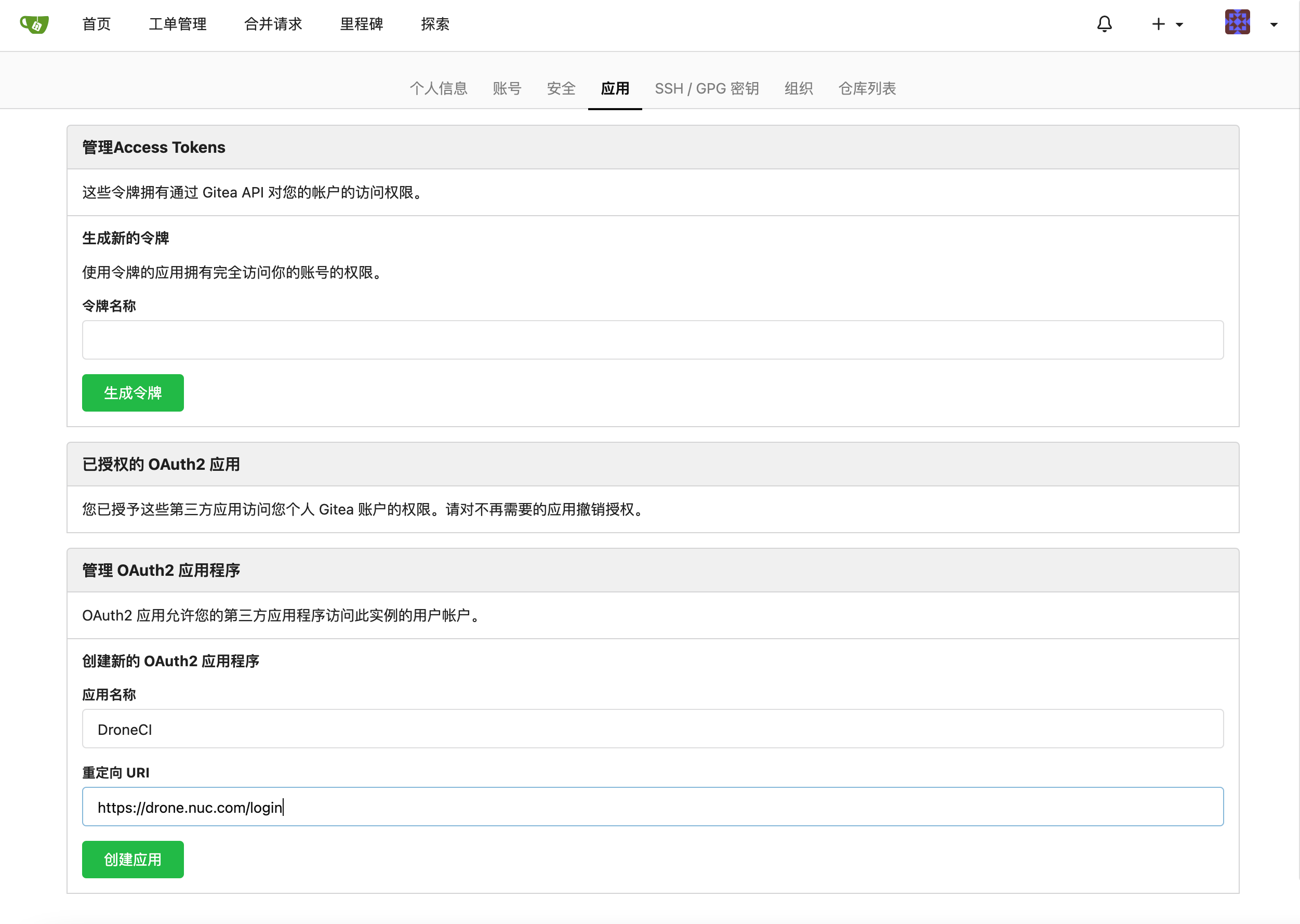
配置 Gitea 的 OAuth 应用
在名称处填写“DroneCI”,重定向 URI 填写之前的配置的域名,并带上 /login 路径:
1
|
http://drone.nuc.com/login
|
点击提交,可以看到我们需要的 OAuth ClientID / Secret 信息已经生成完毕。
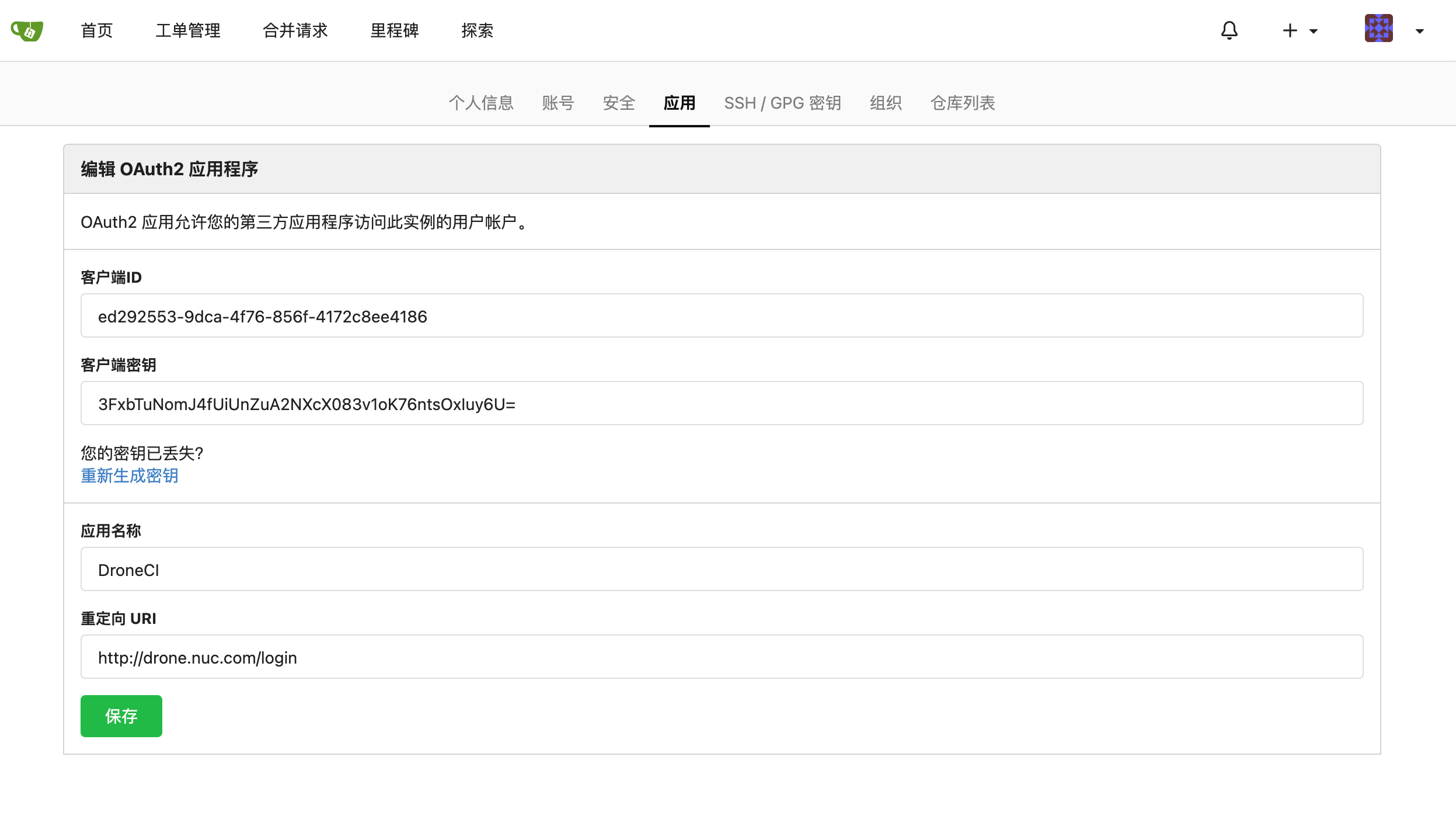
获取创建好的 OAuth Key
将内容更新到我们上文中的 Drone Server 的配置中,我们开始对 Drone 进行配置。
完成 Drone 的最后配置
对 Drone Server 的 .env 配置中的信息进行更新,将上面的 OAuth 信息填入配置中:
1
2
|
DRONE_GITEA_CLIENT_ID=ed292553-9dca-4f76-856f-4172c8ee4186
DRONE_GITEA_CLIENT_SECRET=3FxbTuNomJ4fUiUnZuA2NXcX083v1oK76ntsOxIuy6U=
|
然后使用 docker-compose up -d 启动服务,顺便进入 Drone Runner 目录,将 Runner 也使用 docker-compose up -d 一并启动,等待大概五秒钟,浏览器访问我们配置的 CI 服务域名:drone.nuc.com,会看到浏览器自动跳转到了 OAuth 配置授权页面:
 drone_ci 界面展示:
drone_ci 界面展示:
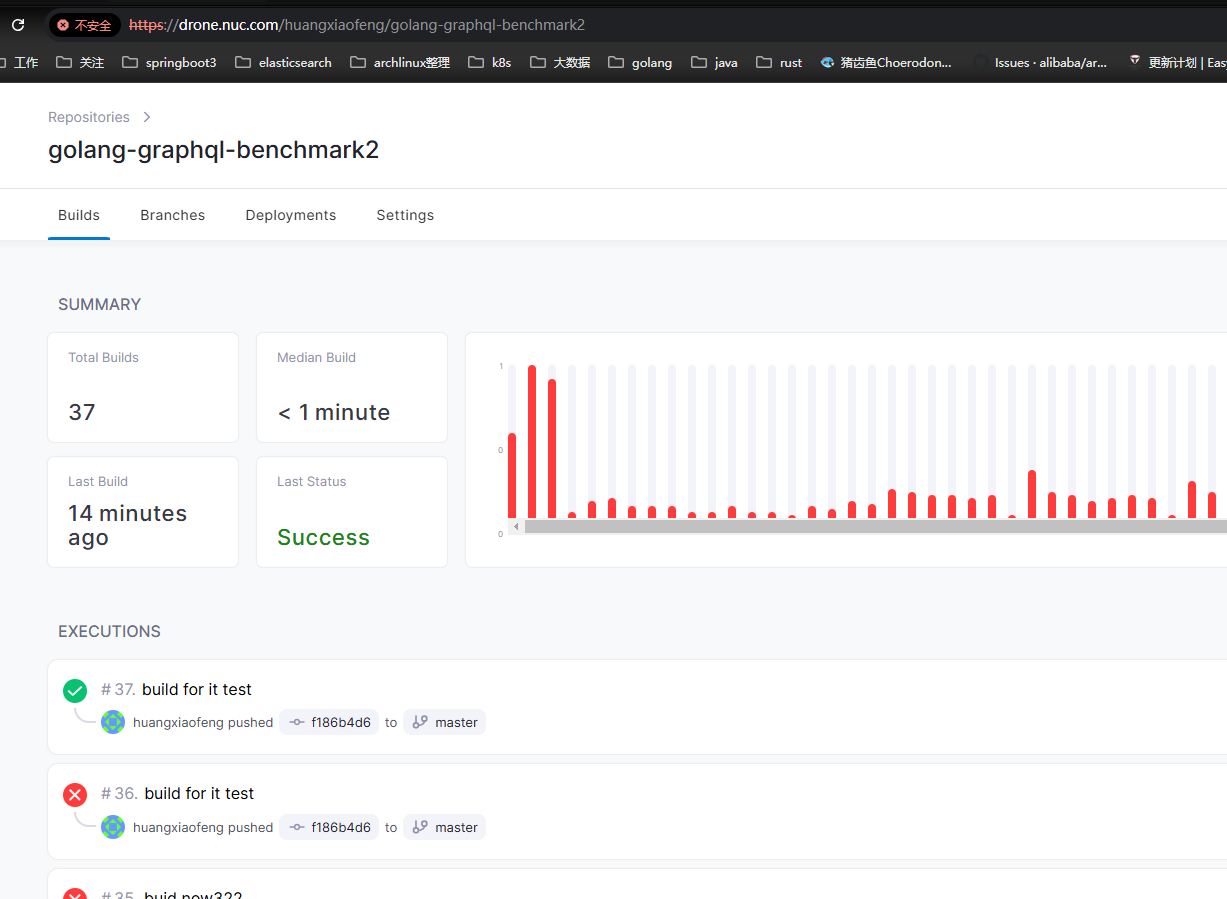
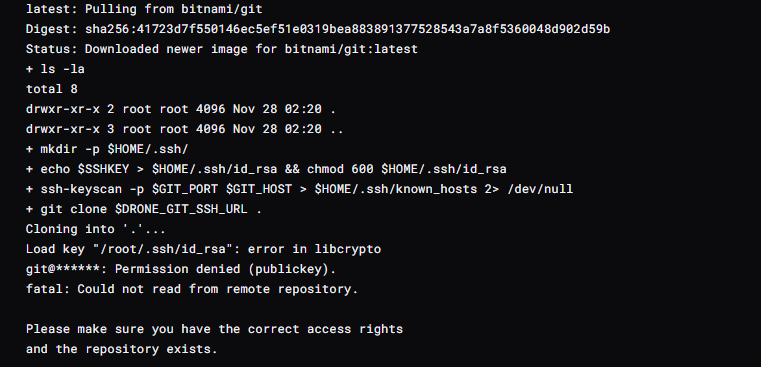
创建测试项目进行使用,首先配置key。sshkey需要做以下处理,注意这个key如果配置的有问题就会出现加载密钥“/root/.ssh/id_ed25519”时出错:libcrypto 中出现错误
1
|
-----BEGIN OPENSSH PRIVATE KEY-----\nb3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn\nNhAAAAAwEAAQAAAYEAu3p3CjElYzQF6xPcGVRBOqEbG1LfzwEVpgBcH3kkSJp25OFy+nq9\nbvr9uWAGGs/wdu7cI/dw9vJLLBqKqnIwbPkEa2hv1Kv5sXsqj+rsz1j0MhlbGVz+KTI5Nl\nRRNlgvN1wv80nViY6wDH+0qxZViUZcsmhEQKtPXPy388FyoKgAnJIsAETjGgwYNOQeItVm\nNv8m68Dd1wLXAVFuoFEsj8VOGLx1Fhn9ZqEZPfo/0w9LEoucBgn0q6LiaJdj/4YCzslgUq\necMJM43fmAsqjrL1vFaAQzAQv07wNmyhgw4G34cJrnAwTBEo5/NQEq2E6YzJA0hApJykJD\nZDwAkJpikEt5Km0I5T2g1qYExARz+m1o3Mva9TcBLPw+0Z00i16LUa/XS1tUV/8w8AzMS0\n544nF4LEBM3LFSJWSDmx8TcO2xOcksMJZ1+AfsIeD+IVgVgu1RmGyf0LPDUjPrIg9W+507\nINmd84Q8qi7+URfoWdz7XohcpzmxU0uYxopxAdbTAAAFgAizc08Is3NPAAAAB3NzaC1yc2\nEAAAGBALt6dwoxJWM0BesT3BlUQTqhGxtS388BFaYAXB95JEiaduThcvp6vW76/blgBhrP\n8Hbu3CP3cPbySywaiqpyMGz5BGtob9Sr+bF7Ko/q7M9Y9DIZWxlc/ikyOTZUUTZYLzdcL/\nNJ1YmOsAx/tKsWVYlGXLJoRECrT1z8t/PBcqCoAJySLABE4xoMGDTkHiLVZjb/JuvA3dcC\n1wFRbqBRLI/FThi8dRYZ/WahGT36P9MPSxKLnAYJ9Kui4miXY/+GAs7JYFKnnDCTON35gL\nKo6y9bxWgEMwEL9O8DZsoYMOBt+HCa5wMEwRKOfzUBKthOmMyQNIQKScpCQ2Q8AJCaYpBL\neSptCOU9oNamBMQEc/ptaNzL2vU3ASz8PtGdNItei1Gv10tbVFf/MPAMzEtOeOJxeCxATN\nyxUiVkg5sfE3DtsTnJLDCWdfgH7CHg/iFYFYLtUZhsn9Czw1Iz6yIPVvudOyDZnfOEPKou\n/lEX6Fnc+16IXKc5sVNLmMaKcQHW0wAAAAMBAAEAAAGACjuH7cV67ewz+n2uAK/pk4KhkR\n832fuMK/BPFuSsx02u+ZUYinVSi5Elcg28p4/75vHokAn8X24gDjswoFb1L61zwU0E9Y2h\nZj97tjkzTankQivCHiNGOAdmugFmIVo00Ye1kkjQX96q2zPJL6Fbb8+oVZB9US5IeaHNhH\n9le0FQLzuHLUiVQKGyXIiq4GnXV18bx7hSI18jTw4bxKJJlVtGhPEcTuWCQCzAzPIws5td\nFJkMHgRDF28ffmfs7FBrFNqnEF7yblBilvsp3PNrpcQS6XUiW5cTnPzu/RgpJ/VM6Moe4Y\n99kN6lxU1YZdZ1MbWhXpv4bUXzyD+563uFZU4pueC8PVy8IMPFxYZ8zU84BSqO1ebr1fjO\nw5At1pX8wnrK2A9tohwABbUtd5FFYD77WPte7rvYZ+Gs35vsWd2ax+DJ+8k8jh0Q/7DNsL\nzoMSxsgR/k+gZENTpCP52bpBx6oPU7CWfFlcqRPzu72P5D7tbIw32csowgEkuGF635AAAA\nwQC1RKLtJhOUMdz3XIe54aSC0aQpaeFl1JpM9OZJ7PkzseJlhLC/kColzbz4JBK48ug/ab\nWRs+jTeZS14X04wMNpXAlBlKdVAHuBIUQBVgtuVoiEO3noClT+tt5vWoPOAx3NSigwoRzi\nXL1dcgzwNnfEJiWFyAbSl28H5Zb5s5lQ7LlYJOvfo8lfPx+iLIJRVLRbv15uOFJoE0WDLi\nGn6tnp+2XMfg6m4ZrVAXW7r272XOMqtJhnDWk0H/ooA0EhNEgAAADBAOjmrfrLJheVJLN0\nbdbBQMFkvyceNTp0DFyGqkY7pfSDPrbxLXub5s7SuUJ0CjYZh78cc0XT4dnP8I8+5BX8Y6\ngFz0EamqRkkNUOLQ1Uctu0HIZFWFhxo3RdqbFiYGVAyBvbJ2Gcpq9t9h0Tzx5Sx+c3Kzpu\n+RB3mQ3epErBicloWJponn05JO+ZVTJVAp1uMDHHI1akskcaNbebVl9K7IyWiVCjOr9Cfh\n3XxGy0JgW8ro33TlwMMSSWVulCQF70ZwAAAMEAzhKCmv3TjBZrPRLcmh0DTdnGqavRx+wO\n7aBOuivSjY6gYjRN/AoWSN8CtmzxdPyGe/ddB7mEQ0usNNqabKE5mxTaEvEW3ILJnmgRcq\n3VelRvTq7f55PJubfvxsYAG9KpoH/tVEpm1sFQdWsgw3BHvScBlfGurpyxKtcxBk6C3tit\nUzAKQo6aSzt7U+ZYlkOTb+Ej6W/kPUphxMm26GwnUprcFDZjTT90b0XnY1pzDOhWwVfCDb\n7FYKzpO5EE0ma1AAAAB0Ryb25lQ0kBAgM=\n-----END OPENSSH PRIVATE KEY-----\n
|
注意必须用\n链接在一起。
git_server_host : gitea.nuc.com
git_server_port: 22
通过密钥文件¶
前置工作:同样是添加私钥文件内容到 Secrets 中,但稍有不同的是,由于需要通过填入的字符串生成本次构建临时的私钥文件,特别注意需要将 id_rsa 内容的每一个换行替换为字符串 \n (直接粘贴进去会丢掉换行特征,因此需要转义),类似下面的样子,然后再粘贴到 Secrets 中
drone.yaml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
cat .drone.yml
kind: pipeline
name: testing
clone:
disable: true
steps:
- name: "Checkout"
image: bitnami/git
pull: if-not-exists
environment:
SSHKEY:
from_secret: drone_ci_sshkey_file
GIT_HOST:
from_secret: git_server_host
GIT_PORT:
from_secret: git_server_port
commands:
- ls -la
- mkdir -p $HOME/.ssh/
- echo $SSHKEY > $HOME/.ssh/id_rsa && chmod 600 $HOME/.ssh/id_rsa
- ssh-keyscan -p $GIT_PORT $GIT_HOST > $HOME/.ssh/known_hosts 2> /dev/null
- cat $HOME/.ssh/id_rsa
- git clone $DRONE_GIT_SSH_URL .
- git submodule update --init --recursive
- git -c advice.detachedHead=false checkout $DRONE_COMMIT
- git status
- name: testing
image: golang:1.15
environment:
GO111MODULE: on
commands:
- go test -v -bench=Master -benchmem
- go test -v -bench=Route -benchmem
[WARN] - (starship::utils): Executing command "/home/xfhuang/.gvm/gos/go1.22/bin/go" timed out.
[WARN] - (starship::utils): You can set command_timeout in your config to a higher value to allow longer-running commands to keep executing.
|
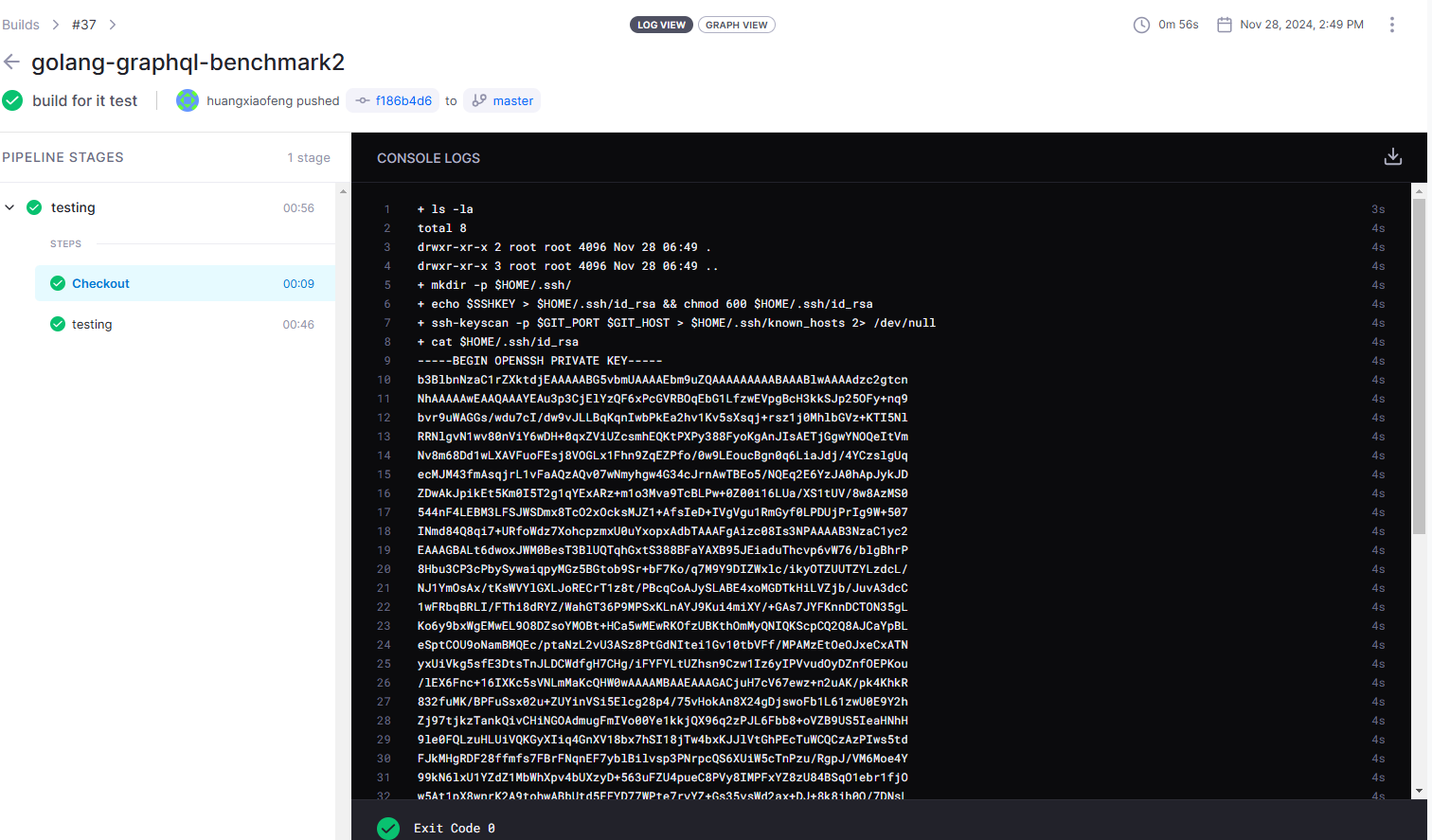
注意观察。
docker镜像mirror
https://blog.csdn.net/llc580231/article/details/139979603
https://dockerproxy.net/docs
注意这里本地链接到gitea有一个需要操作的文档:
https://blog.csdn.net/muxuen/article/details/141407520
其中需要自己建一下软连接
1
2
|
ls -all /app/gitea/gitea
rwxrwxrwx 1 xfhuang xfhuang 20 B Wed Nov 27 17:06:13 2024 /app/gitea/gitea ⇒ /usr/local/bin/gitea
|
总结一下记录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
|
sudo useradd -m -G wheel -s /bin/bash git
id git
uid=1002(git) gid=1002(git) groups=1002(git),998(wheel)
sudo su - git
[git@xfhuang-pc ~]$ sudo -u git ssh-keygen -t rsa -b 4096 -C "Gitea Host Key"
Generating public/private rsa key pair.
Enter file in which to save the key (/home/git/.ssh/id_rsa):
Created directory '/home/git/.ssh'.
Enter passphrase for "/home/git/.ssh/id_rsa" (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/git/.ssh/id_rsa
Your public key has been saved in /home/git/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:QrgKPWPteMZP8Y+Pt/OUebGgNfusE29gmeoVa0XBXFo Gitea Host Key
The key's randomart image is:
+---[RSA 4096]----+
| o..E|
| . o+ |
| . . o |
| . . o . |
|. = o o S =oo |
| o B + o*X o |
| o = . . .oO+o |
| o o +++.+o |
| . o+=+o+o |
+----[SHA256]-----+
[git@xfhuang-pc ~]$ echo "$(cat /home/git/.ssh/id_rsa.pub)" >> /home/git/.ssh/authorized_keys
[git@xfhuang-pc ~]$ sudo vim /usr/local/bin/gitea
#添加以下内容
cat /usr/local/bin/gitea
ssh -p 2222 -o StrictHostKeyChecking=no git@127.0.0.1 "SSH_ORIGINAL_COMMAND=\"$SSH_ORIGINAL_COMMAND\" $0 $@"
echo "$(cat /home/git/.ssh/id_rsa.pub)" >> /home/git/.ssh/authorized_keys
[git@xfhuang-pc ~]$ sudo vim /usr/local/bin/gitea
[git@xfhuang-pc ~]$ sudo chmod 777 /usr/local/bin/gitea
测试ssh链接
ssh -T git@gitea.nuc.com
Hi there, huangxiaofeng! You've successfully authenticated with the key named hxf168482@gmail.com, but Gitea does not provide shell access.
If this is unexpected, please log in with password and setup Gitea under another user.
#出现上面这个内容就代表成功
|
 至此就基本完成了老配置 Traefik 的所有功能,后续如果有“规则”需要变化,只需要修改刚刚这几个文件即可,而无需重启 Traefik 就能生效了。
至此就基本完成了老配置 Traefik 的所有功能,后续如果有“规则”需要变化,只需要修改刚刚这几个文件即可,而无需重启 Traefik 就能生效了。


 drone_ci 界面展示:
drone_ci 界面展示:


