如果在 K8S 集群中安装 Istio,最后则是通过官方 demo bookinfo 简单展示 Istio 如何使用。
本文主要为 Istio 环境部署,暂时不管 Isito 是怎么用的,怎么实现的,先跑起来再说。
文章分为三部分:
- 1)安装 K8S 集群
- 2)安装 Istio
- 3)部署官方 Demo 体验 Istio
2. Istio 安装
getting-start
下载 Istio
下载 Istio,可以去 release 页面 手动下载并解压,或者通过官方提供的脚本自动下载解压:
1
|
curl -L https://istio.io/downloadIstio | sh -
|
国内网络问题,脚本大概率下载不动,需要手动下载。
1
|
wget https://github.com/istio/istio/releases/download/1.18.1/istio-1.20.1-linux-amd64.tar.gz tar -zxvf istio-1.20.1-linux-amd64.tar.gz
|
压缩包里包含以下内容
1
2
3
4
5
6
7
8
9
10
|
[root@vela istio-1.20.1]# ll
drwxrwxrwx - xfhuang xfhuang 8 Dec 2023 bin
drwxrwxrwx - xfhuang xfhuang 9 Jan 15:32 example_certs1
drwxrwxrwx - xfhuang xfhuang 9 Jan 15:33 example_certs2
.rwxrwxrwx 11k xfhuang xfhuang 8 Dec 2023 LICENSE
.rwxrwxrwx 956 xfhuang xfhuang 8 Dec 2023 manifest.yaml
drwxrwxrwx - xfhuang xfhuang 8 Dec 2023 manifests
.rwxrwxrwx 6.6k xfhuang xfhuang 8 Dec 2023 README.md
drwxrwxrwx - xfhuang xfhuang 8 Dec 2023 samples
drwxrwxrwx - xfhuang xfhuang 8 Dec 2023 tools
|
各个目录的作用:
- bin:存放的是 istioctl 工具
- manifests:相关 yaml 用于部署 Istio 的
- samples:一些 Demo 用的 yaml
- tools:一些工具,暂时使用不到
先将istioctl工具 cp 到 bin 目录下,便于后续使用 istioctl 命令。
1
|
sudo cp bin/istioctl /usr/local/bin/
|
安装 Istio
由于易用性的问题,Istio 废弃了以前的 Helm 安装方式,现在使用 istioctl 即可一键安装。
Istio 提供了以下配置档案(configuration profile)供不同场景使用,查看当前内置的 profile:
1
2
3
4
5
6
7
8
9
10
11
|
$ istioctl profile list
Istio configuration profiles:
ambient
default
demo
empty
external
minimal
openshift
preview
remote
|
具体每个 profile 包含哪些组件,可以使用istioctl profile dump命令查看:
1
|
$ istioctl profile dump demo
|
输出比较多,就不展示了
对于演示环境,我们直接安装 demo 版本就可以了
1
|
istioctl install --set profile=demo -y
|
安装可能需要一些时间,耐心等待即可,安装完成后,输出如下:
1
2
3
4
5
6
|
istioctl install --set profile=demo -y
Error: failed to install manifests: errors occurred during operation: creating default tag would conflict:
Error [IST0139] (MutatingWebhookConfiguration istio-sidecar-injector) Webhook overlaps with others: [istio-revision-tag-default/namespace.sidecar-injector.istio.io]. This may cause injection to occur twice.
Error [IST0139] (MutatingWebhookConfiguration istio-sidecar-injector) Webhook overlaps with others: [istio-revision-tag-default/object.sidecar-injector.istio.io]. This may cause injection to occur twice.
Error [IST0139] (MutatingWebhookConfiguration istio-sidecar-injector) Webhook overlaps with others: [istio-revision-tag-default/rev.namespace.sidecar-injector.istio.io]. This may cause injection to occur twice.
Error [IST0139] (MutatingWebhookConfiguration istio-sidecar-injector) Webhook overlaps with others: [istio-revision-tag-default/rev.object.sidecar-injector.istio.io]. This may cause injection to occur twice.
|
报错了
1
2
3
4
5
6
|
kubectl get MutatingWebhookConfiguration
NAME WEBHOOKS AGE
cert-manager-webhook 1 89d
flink-operator-default-webhook-configuration 1 89d
istio-revision-tag-default 4 97d
istio-sidecar-injector
|
1
|
kubectl delete MutatingWebhookConfiguration istio-revision-tag-default
|
再来一次执行
1
2
3
4
5
6
|
istioctl install --set profile=demo -y
✔ Istio core installed
✔ Istiod installed
✔ Egress gateways installed
✔ Ingress gateways installed
✔ Installation complete Made this installation the default for injection and validation.
|
部署完成后,还有很重要的一步:
给命名空间打上 label,告诉 Istio 在部署应用的时候,自动注入 Envoy 边车代理:
1
|
kubectl label namespace default istio-injection=enabled
|
验证是否安装成功
安装后可以验证是否安装正确。
1
2
3
4
5
6
|
# 先根据安装的profile导出manifest
istioctl manifest generate --set profile=demo > $HOME/generated-manifest.yaml
# 然后根据验证实际环境和manifest文件是否一致
istioctl verify-install -f $HOME/generated-manifest.yaml
# 出现下面信息则表示验证通过
✔ Istio is installed and verified successfully
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
istioctl verify-install -f $HOME/generated-manifest.yaml
✔ CustomResourceDefinition: authorizationpolicies.security.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: destinationrules.networking.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: envoyfilters.networking.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: gateways.networking.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: istiooperators.install.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: peerauthentications.security.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: proxyconfigs.networking.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: requestauthentications.security.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: serviceentries.networking.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: sidecars.networking.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: telemetries.telemetry.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: virtualservices.networking.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: wasmplugins.extensions.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: workloadentries.networking.istio.io.istio-system checked successfully
✔ CustomResourceDefinition: workloadgroups.networking.istio.io.istio-system checked successfully
✔ ServiceAccount: istio-egressgateway-service-account.istio-system checked successfully
✔ ServiceAccount: istio-ingressgateway-service-account.istio-system checked successfully
✔ ServiceAccount: istio-reader-service-account.istio-system checked successfully
✔ ServiceAccount: istiod.istio-system checked successfully
✔ ClusterRole: istio-reader-clusterrole-istio-system.istio-system checked successfully
✔ ClusterRole: istiod-clusterrole-istio-system.istio-system checked successfully
✔ ClusterRole: istiod-gateway-controller-istio-system.istio-system checked successfully
✔ ClusterRoleBinding: istio-reader-clusterrole-istio-system.istio-system checked successfully
✔ ClusterRoleBinding: istiod-clusterrole-istio-system.istio-system checked successfully
✔ ClusterRoleBinding: istiod-gateway-controller-istio-system.istio-system checked successfully
✔ ValidatingWebhookConfiguration: istio-validator-istio-system.istio-system checked successfully
✔ ConfigMap: istio.istio-system checked successfully
✔ ConfigMap: istio-sidecar-injector.istio-system checked successfully
✔ MutatingWebhookConfiguration: istio-sidecar-injector.istio-system checked successfully
✔ Deployment: istio-egressgateway.istio-system checked successfully
✔ Deployment: istio-ingressgateway.istio-system checked successfully
✔ Deployment: istiod.istio-system checked successfully
✔ PodDisruptionBudget: istio-egressgateway.istio-system checked successfully
✔ PodDisruptionBudget: istio-ingressgateway.istio-system checked successfully
✔ PodDisruptionBudget: istiod.istio-system checked successfully
✔ Role: istio-egressgateway-sds.istio-system checked successfully
✔ Role: istio-ingressgateway-sds.istio-system checked successfully
✔ Role: istiod.istio-system checked successfully
✔ RoleBinding: istio-egressgateway-sds.istio-system checked successfully
✔ RoleBinding: istio-ingressgateway-sds.istio-system checked successfully
✔ RoleBinding: istiod.istio-system checked successfully
✔ Service: istio-egressgateway.istio-system checked successfully
✔ Service: istio-ingressgateway.istio-system checked successfully
✔ Service: istiod.istio-system checked successfully
Checked 15 custom resource definitions
Checked 3 Istio Deployments
✔ Istio is installed and verified successfully
|
查看一下安装了些什么东西:
1
2
3
4
5
|
kubectl get pods -n istio-system
NAME READY STATUS RESTARTS AGE
istio-egressgateway-6dc59b5b45-84tlt 1/1 Running 0 2m21s
istio-ingressgateway-654796fd4f-hfvfs 1/1 Running 0 2m21s
istiod-6b6f4654c4-69ws4 1/1 Running 0 2m25s
|
可以看到只安装了出入站网关以及最重要的 Istiod 服务。
再看下 CRD 情况
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
kubectl get crds |grep istio
authorizationpolicies.security.istio.io 2024-01-08T09:28:15Z
destinationrules.networking.istio.io 2024-01-08T09:28:15Z
envoyfilters.networking.istio.io 2024-01-08T09:28:15Z
gateways.networking.istio.io 2024-01-08T09:28:15Z
istiooperators.install.istio.io 2024-01-08T09:28:16Z
peerauthentications.security.istio.io 2024-01-08T09:28:15Z
proxyconfigs.networking.istio.io 2024-01-08T09:28:15Z
requestauthentications.security.istio.io 2024-01-08T09:28:15Z
serviceentries.networking.istio.io 2024-01-08T09:28:15Z
sidecars.networking.istio.io 2024-01-08T09:28:15Z
telemetries.telemetry.istio.io 2024-01-08T09:28:15Z
virtualservices.networking.istio.io 2024-01-08T09:28:15Z
wasmplugins.extensions.istio.io 2024-01-08T09:28:15Z
workloadentries.networking.istio.io 2024-01-08T09:28:15Z
workloadgroups.networking.istio.io 2024-01-08T09:28:15Z
|
这些就是 istio 需要用到的 CRD 了,比较常见的比如:
- gateways
- virtualservices
- destinationrules
- …
部署 Dashboard
3. 部署 bookinfo 应用
官方提供了 bookinfo 应用来演示 Istio 相关功能。
部署应用
1
|
kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml
|
输出如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml
service/details unchanged
serviceaccount/bookinfo-details unchanged
deployment.apps/details-v1 unchanged
service/ratings unchanged
serviceaccount/bookinfo-ratings unchanged
deployment.apps/ratings-v1 unchanged
service/reviews unchanged
serviceaccount/bookinfo-reviews unchanged
deployment.apps/reviews-v1 unchanged
deployment.apps/reviews-v2 unchanged
deployment.apps/reviews-v3 unchanged
service/productpage unchanged
serviceaccount/bookinfo-productpage unchanged
deployment.apps/productpage-v1 unchanged
|
在 default 命名空间创建了应用对应的 service 和 deployment。
服务启动需要一定时间,可通过以下命令进行查看:
1
2
3
4
5
6
7
8
9
|
kubectl get pods
NAME READY STATUS RESTARTS AGE
details-v1-698d88b-97bkt 2/2 Running 0 104m
flink-kubernetes-operator-65d5bf6d48-wcq2j 3/3 Running 74 (6d1h ago) 89d
productpage-v1-675fc69cf-wr4bd 2/2 Running 0 104m
ratings-v1-6484c4d9bb-cvdl8 2/2 Running 0 104m
reviews-v1-5b5d6494f4-bzqsh 2/2 Running 0 104m
reviews-v2-5b667bcbf8-4txw6 2/2 Running 0 104m
reviews-v3-5b9bd44f4-rbhgv 2/2 Running 0 104m
|
等 pod 都启动后,通过以下命令测试应用是否正常启动了:
1
|
kubectl exec "$(kubectl get pod -l app=ratings -o jsonpath='{.items[0].metadata.name}')" -c ratings -- curl -s productpage:9080/productpage | grep -o "<title>.*</title>"
|
输出以下内容就算成功
1
|
<title>Simple Bookstore App</title>
|
部署网关
此时,BookInfo 应用已经部署,但还不能被外界访问。需要借助网关才行
1
|
kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml
|
输出如下:
1
2
3
|
kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml
gateway.networking.istio.io/bookinfo-gateway unchanged
virtualservice.networking.istio.io/bookinfo unchanged
|
可以看到, 这里部署了一个网关(gateway)和一个虚拟服务(virtualservice)。
这里不知道也没关系,后续文章会讲的 😁
此时在浏览器中,输入http://localhost/productpage应该可以访问到具体页面了。
外部访问则需要通过 NodePort 访问:
1
2
3
4
5
|
kubectl -n istio-system get svc istio-ingressgateway
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-ingressgateway LoadBalancer 10.233.41.37 <pending> 15021:30882/TCP,80:32746/TCP,443:31231/TCP,31400:32093/TCP,15443:32172/TCP 4m58s
echo http://10.7.20.12:30754/productpage
http://10.7.20.12:30754/productpage
|
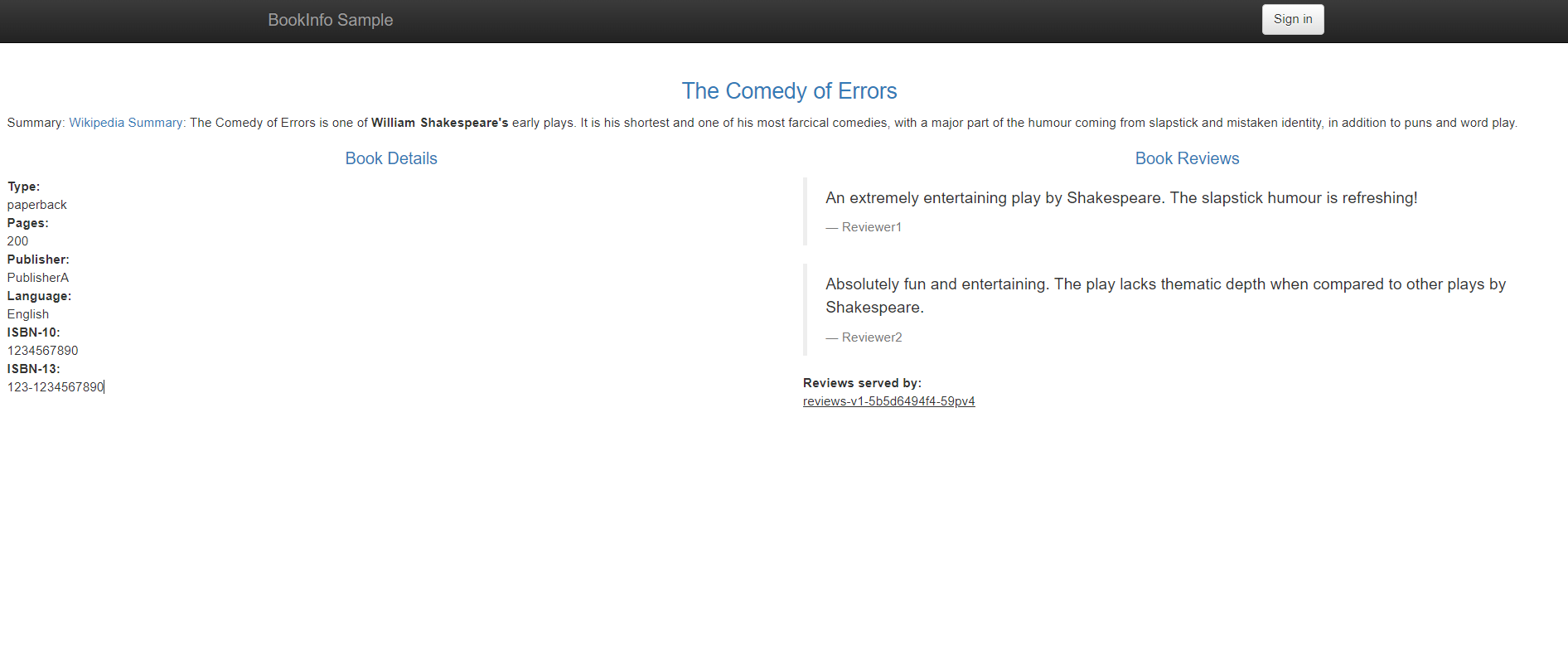
可以看到,80 端口对应的 NodePort 为 32746,那么直接访问的 URL 就是:http://$IP:32746/productpage。
能看到以下界面就算成功:
4. Dashboard
Istio 也提供了 Dashboard,可以通过 UI 界面更加方便的进行管理,安装命令如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
kubectl apply -f samples/addons
serviceaccount/grafana created
configmap/grafana created
service/grafana created
deployment.apps/grafana created
configmap/istio-grafana-dashboards created
configmap/istio-services-grafana-dashboards created
deployment.apps/jaeger created
service/tracing created
service/zipkin created
service/jaeger-collector created
serviceaccount/kiali created
configmap/kiali created
clusterrole.rbac.authorization.k8s.io/kiali-viewer created
clusterrole.rbac.authorization.k8s.io/kiali created
clusterrolebinding.rbac.authorization.k8s.io/kiali created
role.rbac.authorization.k8s.io/kiali-controlplane created
rolebinding.rbac.authorization.k8s.io/kiali-controlplane created
service/kiali created
deployment.apps/kiali created
serviceaccount/loki created
configmap/loki created
configmap/loki-runtime created
service/loki-memberlist created
service/loki-headless created
service/loki created
statefulset.apps/loki created
serviceaccount/prometheus created
configmap/prometheus created
clusterrole.rbac.authorization.k8s.io/prometheus created
clusterrolebinding.rbac.authorization.k8s.io/prometheus created
service/prometheus created
deployment.apps/prometheus created
|
等待安装完成
1
2
|
kubectl rollout status deployment/kiali -n istio-system
deployment "kiali" successfully rolled out
|
访问 bashboard:
该命令会自动打开浏览器,若失败则手动访问。
外部访问则把 service 改成 nodeport 类型即可
1
|
kubectl -n istio-system patch svc kiali -p '{"spec":{"type":"NodePort"}}'
|
查看修改后的端口
1
2
3
|
kubectl -n istio-system get svc kiali
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kiali NodePort 10.233.16.184 <none> 20001:32276/TCP,9090:31874/TCP 99s
|
访问 http://$IP:32276 即可,界面长这样:
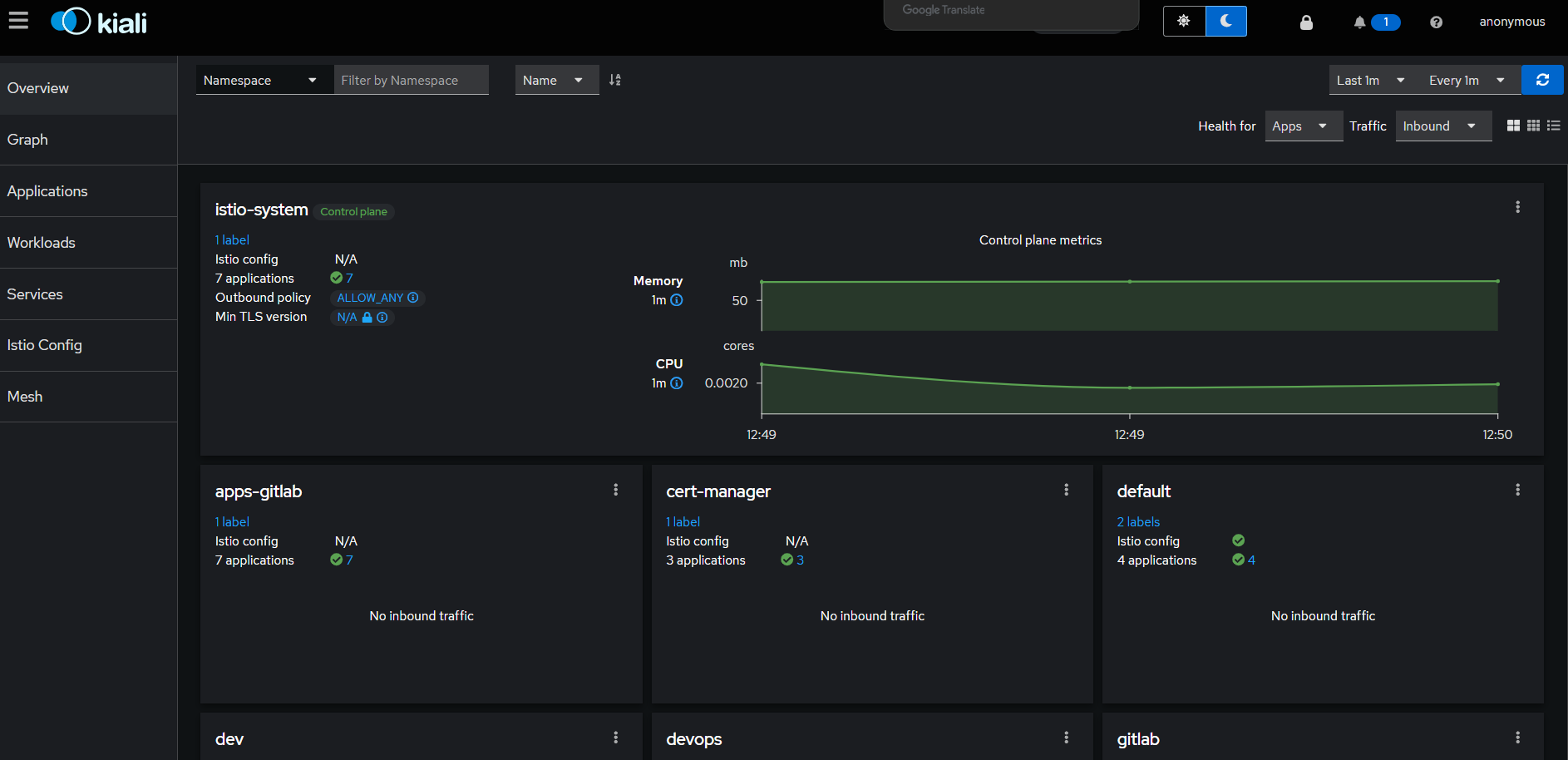
在主界面可以看到部署的服务以及请求量、资源使用量等情况。
在 Graph 界面则能够看到,服务间流量分发情况。
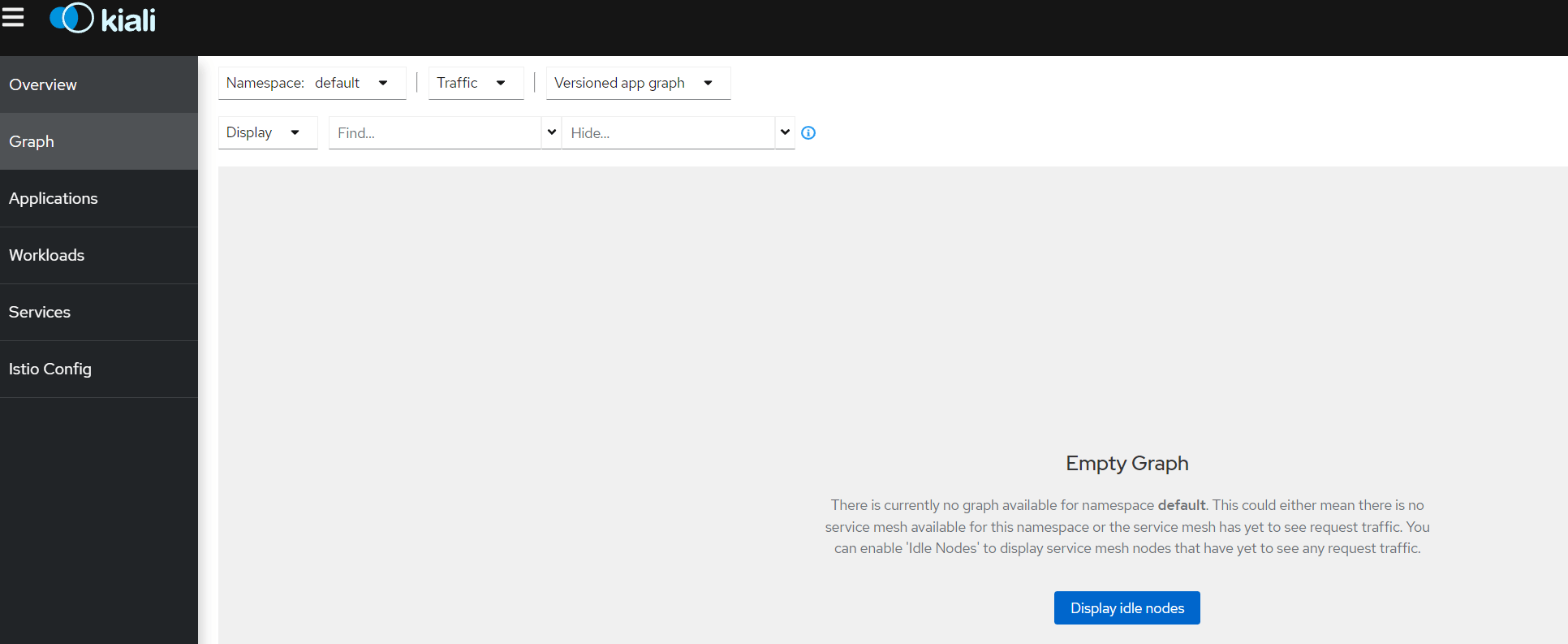
由于之前部署的 bookinfo 服务没怎么访问,所以界面是空白的,先通过 curl 命令访问一下
1
2
3
|
clusterIP=$(kubectl -n istio-system get svc istio-ingressgateway -ojsonpath='{.spec.clusterIP}')
for i in $(seq 1 100); do curl -s -o /dev/null "http://$clusterIP:80/productpage"; done
|
如何确定入站 IP 和端口
1
2
3
4
5
6
7
8
9
10
11
12
|
kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="http2")].nodePort}'
30754%
kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="https")].nodePort}'
32360%
kubectl get po -l istio=ingressgateway -n istio-system -o jsonpath='{.items[0].status.hostIP}'
192.7.20.12%
http://192.7.20.245:30754/productpage
|
再次查看就可以看到流量分发情况了
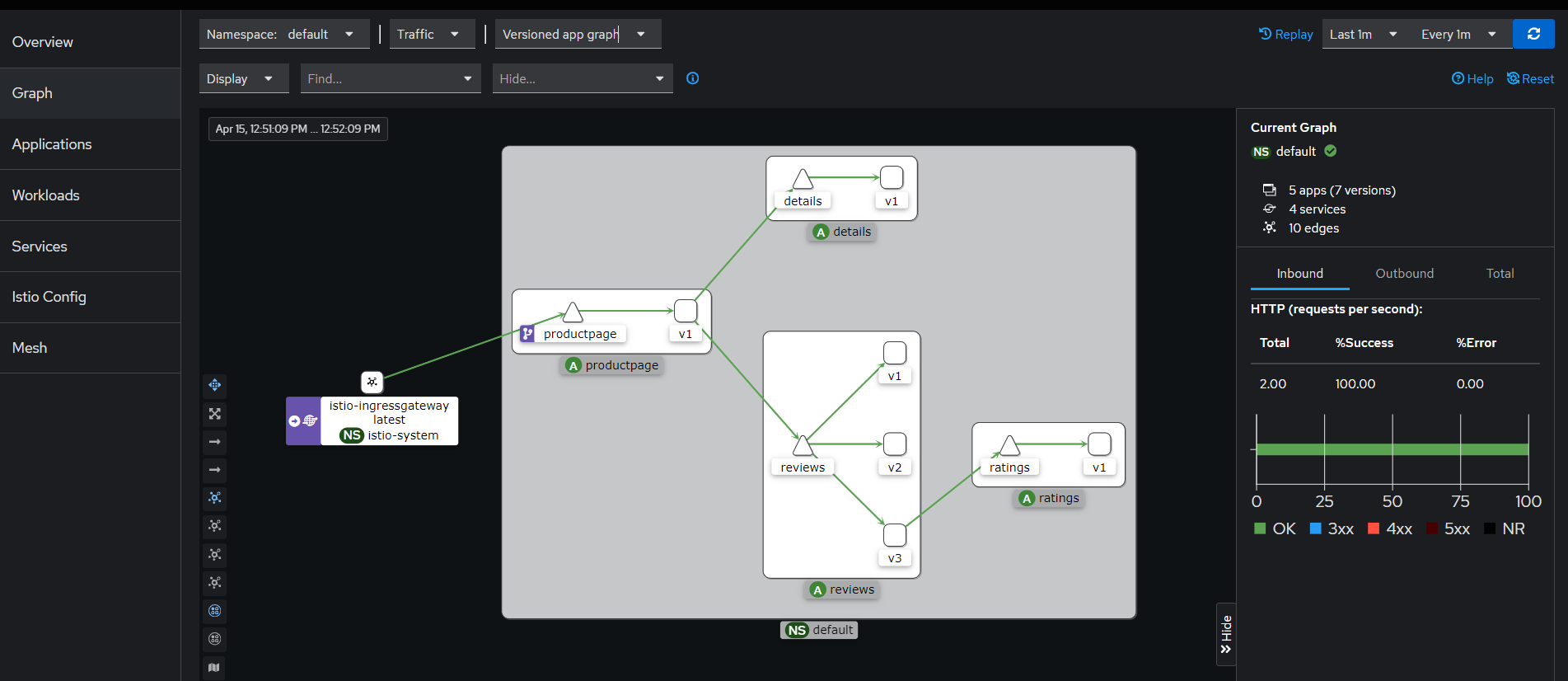
5. 卸载 Istio
istiod 中的’d’ 代表 daemon
istio ingress gateway
istio ingress gateway 是进入集群的大门,外部要访问网格内部需要从这个 ingress gateway 进入
istio egress gateway
istio egress gateway 是出去集群的大门。流量出去的时候走这
卸载 istio
以下命令卸载 Istio 并删除所有相关资源
1
2
|
kubectl delete -f samples/addons
istioctl x uninstall --purge -y
|
删除 namespace
1
|
kubectl delete namespace istio-system
|
移除之前打的 label
1
|
kubectl label namespace default istio-injection-
|
参考文档:



