1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
|
apiVersion: kubeadm.k8s.io/v1beta2
kind: InitConfiguration
localAPIEndpoint:
advertiseAddress: 10.7.9.10
bindPort: 6443
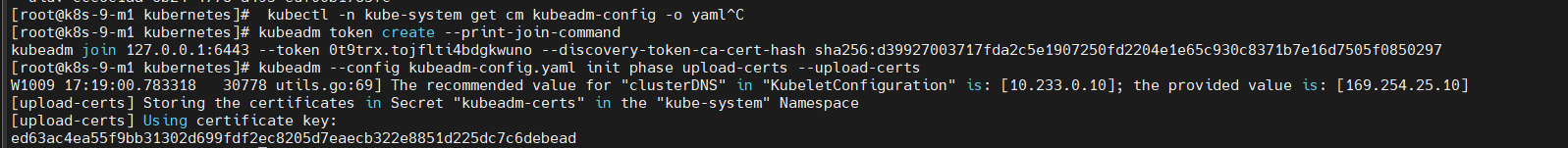
certificateKey: ed63ac4ea55f9bb31302d699fdf2ec8205d7eaecb322e8851d225dc7c6debead
nodeRegistration:
name: k8s-9-m1
taints:
- effect: NoSchedule
key: node-role.kubernetes.io/master
criSocket: /var/run/containerd/containerd.sock
---
apiVersion: kubeadm.k8s.io/v1beta2
kind: ClusterConfiguration
clusterName: cluster.local
etcd:
external:
endpoints:
- https://10.7.9.10:2379
caFile: /etc/ssl/etcd/ssl/ca.pem
certFile: /etc/ssl/etcd/ssl/node-k8s-9-m1.pem
keyFile: /etc/ssl/etcd/ssl/node-k8s-9-m1-key.pem
dns:
type: CoreDNS
imageRepository: k8s.gcr.io
imageTag: v1.8.6
networking:
dnsDomain: cluster.local
serviceSubnet: "10.233.0.0/16"
podSubnet: "10.234.0.0/16"
kubernetesVersion: v1.23.8
controlPlaneEndpoint: 10.7.9.10:6443
certificatesDir: /etc/kubernetes/ssl
imageRepository: k8s.gcr.io
apiServer:
extraArgs:
default-not-ready-toleration-seconds: "300"
default-unreachable-toleration-seconds: "300"
anonymous-auth: "True"
authorization-mode: Node,RBAC
bind-address: 0.0.0.0
insecure-port: "0"
apiserver-count: "1"
endpoint-reconciler-type: lease
service-node-port-range: 30000-32767
service-cluster-ip-range: "10.233.0.0/16"
kubelet-preferred-address-types: "InternalDNS,InternalIP,Hostname,ExternalDNS,ExternalIP"
profiling: "False"
request-timeout: "1m0s"
enable-aggregator-routing: "False"
storage-backend: etcd3
allow-privileged: "true"
audit-policy-file: /etc/kubernetes/audit-policy/apiserver-audit-policy.yaml
audit-log-path: "/var/log/audit/kube-apiserver-audit.log"
audit-log-maxage: "30"
audit-log-maxbackup: "10"
audit-log-maxsize: "100"
tls-cipher-suites: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_GCM_SHA256
event-ttl: 1h0m0s
extraVolumes:
- name: audit-policy
hostPath: /etc/kubernetes/audit-policy
mountPath: /etc/kubernetes/audit-policy
- name: audit-logs
hostPath: /var/log/kubernetes/audit
mountPath: /var/log/audit
readOnly: false
- name: etc-pki-tls
hostPath: /etc/pki/tls
mountPath: /etc/pki/tls
readOnly: true
- name: etc-pki-ca-trust
hostPath: /etc/pki/ca-trust
mountPath: /etc/pki/ca-trust
readOnly: true
certSANs:
- kubernetes
- kubernetes.default
- kubernetes.default.svc
- kubernetes.default.svc.cluster.local
- 10.233.0.1
- localhost
- 127.0.0.1
- k8s-9-m1
- lb-apiserver.kubernetes.local
- 10.7.9.10
- k8s-9-m1.cluster.local
timeoutForControlPlane: 5m0s
controllerManager:
extraArgs:
node-monitor-grace-period: 40s
node-monitor-period: 5s
cluster-cidr: "10.234.0.0/16"
service-cluster-ip-range: "10.233.0.0/16"
node-cidr-mask-size: "23"
profiling: "False"
terminated-pod-gc-threshold: "12500"
bind-address: 0.0.0.0
leader-elect-lease-duration: 15s
leader-elect-renew-deadline: 10s
configure-cloud-routes: "false"
tls-cipher-suites: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_GCM_SHA256
scheduler:
extraArgs:
bind-address: 0.0.0.0
config: /etc/kubernetes/kubescheduler-config.yaml
tls-cipher-suites: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_GCM_SHA256
extraVolumes:
- name: kubescheduler-config
hostPath: /etc/kubernetes/kubescheduler-config.yaml
mountPath: /etc/kubernetes/kubescheduler-config.yaml
readOnly: true
---
apiVersion: kubeproxy.config.k8s.io/v1alpha1
kind: KubeProxyConfiguration
bindAddress: 0.0.0.0
clientConnection:
acceptContentTypes:
burst: 10
contentType: application/vnd.kubernetes.protobuf
kubeconfig:
qps: 5
clusterCIDR: "10.234.0.0/16"
configSyncPeriod: 15m0s
conntrack:
maxPerCore: 32768
min: 131072
tcpCloseWaitTimeout: 1h0m0s
tcpEstablishedTimeout: 24h0m0s
enableProfiling: False
healthzBindAddress: 0.0.0.0:10256
hostnameOverride: k8s-9-m1
iptables:
masqueradeAll: False
masqueradeBit: 14
minSyncPeriod: 0s
syncPeriod: 30s
ipvs:
excludeCIDRs: []
minSyncPeriod: 0s
scheduler: rr
syncPeriod: 30s
strictARP: False
tcpTimeout: 0s
tcpFinTimeout: 0s
udpTimeout: 0s
metricsBindAddress: 127.0.0.1:10249
mode: ipvs
nodePortAddresses: []
oomScoreAdj: -999
portRange:
udpIdleTimeout: 250ms
---
apiVersion: kubelet.config.k8s.io/v1beta1
kind: KubeletConfiguration
clusterDNS:
- 169.254.25.10
|