生成证书脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=mybns.cn" \
-key ca.key \
-out ca.crt
openssl genrsa -out mybns.cn.key 4096
openssl req -sha512 -new \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=mybns.cn" \
-key mybns.cn.key \
-out mybns.cn.csr
cat > v3.ext <<-EOF
[ req ]
default_bits = 1024
distinguished_name = req_distinguished_name
req_extensions = san
extensions = san
[ req_distinguished_name ]
countryName = CN
stateOrProvinceName = Definesys
localityName = Definesys
organizationName = Definesys
[SAN]
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = tool.mybns.cn
DNS.2 = *.tool.mybns.cn
EOF
openssl x509 -req -sha512 -days 3650 \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in mybns.cn.csr \
-out mybns.cn.crt -extfile v3.ext -extensions SAN
|
一键生成证书,生成证书如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
zsh 🚀 tree
.
├── ca.crt
├── ca.key
├── ca.srl
├── frontend.crt
├── frontend.csr
├── frontend.key
├── generatSSL.sh
├── mybns.cn.crt
├── mybns.cn.csr
├── mybns.cn.key
├── root.crt
├── root.key
├── root.srl
├── server.crt
├── server.csr
├── server.key
└── v3.ext
|
需要将 mybns.cn.crt 导入到信任的证书机构即可,如下图所示
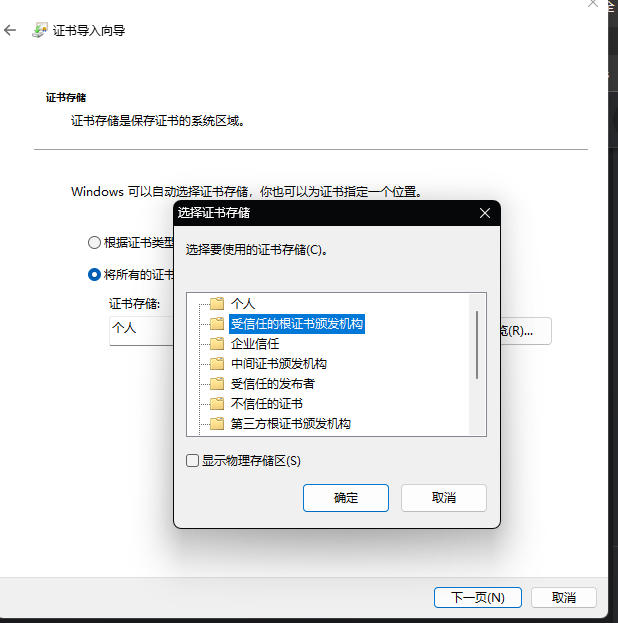 设置 ngingx 的证书位置为:
设置 ngingx 的证书位置为:
1
2
3
|
ssl_certificate /home/*/workspace/go/src/weave/certs/mybns.cn.crt;
#私钥文件名称(此处的私钥文件放在 /etc/nginx/ssl-nginx-qcloud 目录下)
ssl_certificate_key /home/*/workspace/go/src/weave/certs/mybns.cn.key;
|
重启 nginx 和 chrome,再访问网站,就不会有不安全提示。
 设置 ngingx 的证书位置为:
设置 ngingx 的证书位置为: 设置 ngingx 的证书位置为:
设置 ngingx 的证书位置为: